Discuss Scratch
- Discussion Forums
- » Developing Scratch Extensions
- » Test for vulnerabilities please!
![[RSS Feed] [RSS Feed]](//cdn.scratch.mit.edu/scratchr2/static/__74e70580e9dbe93ce1c3f8422dde592d__//djangobb_forum/img/feed-icon-small.png)
- PullJosh
-
 Scratcher
Scratcher
1000+ posts
Test for vulnerabilities please!
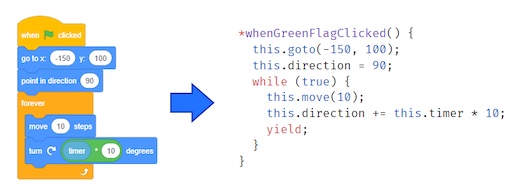
I've created a new extension which pulls an old trick, but does it better than ever before. The extension is called “Open Webpage Extension” and it has one block:
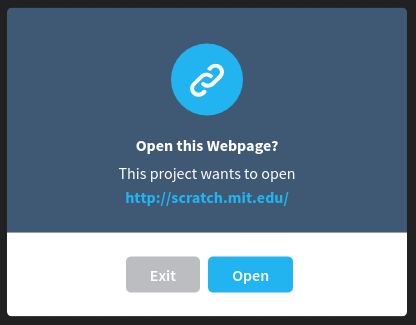
I've done everything I can think of to prevent attacks, but I want some feedback from the community. I'd love everyone to try and create a project which demonstrates how the extension might be able to be used in a malicious way so that I can fix any potential vulnerabilities.
Try it out on ScratchX!
open page at url [http://scratch.mit.edu/] :: extensionThe catch is that I've designed the block to be as safe and secure as possible. When the block runs, a fancy little dialog box pops up, asking the user if they would like to open the page.

I've done everything I can think of to prevent attacks, but I want some feedback from the community. I'd love everyone to try and create a project which demonstrates how the extension might be able to be used in a malicious way so that I can fix any potential vulnerabilities.
Try it out on ScratchX!
- Jonathan50
-
 Scratcher
Scratcher
1000+ posts
Test for vulnerabilities please!
Well, ScratchX links can be dangerous anyway… But I guess if it becomes an official extension then you'll need to be sure it's safe.
Not yet a Knight of the Mu Calculus.
- PullJosh
-
 Scratcher
Scratcher
1000+ posts
Test for vulnerabilities please!
Well, ScratchX links can be dangerous anyway… But I guess if it becomes an official extension then you'll need to be sure it's safe.The hope is that it could one day become an official extension, yeah.
@all I just updated the code so that long urls get clipped to look pretty in the popup.
- helloandgoodbye9
-
 Scratcher
Scratcher
1000+ posts
Test for vulnerabilities please!
You may want to automatically remove /./ - https://blog.library.si.edu/./././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././redir.php?URL=http://crashcrome.com/ looks like blog.library.si.edu/././././././././././././././././././././././././. …, which looks weirld, put has .edu, looking safe to younger scratchers.
Last edited by kaj (Tomorrow 25:61:61) ͪͪͪͪͪͪͪͪͪͪ ͣͣͣͣ ͯͯͯͯYes, its above the line)
- Jonathan50
-
 Scratcher
Scratcher
1000+ posts
Test for vulnerabilities please!
You may want to automatically remove /./ - https://blog.library.si.edu/./././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././redir.php?URL=http://crashcrome.com/ looks like blog.library.si.edu/././././././././././././././././././././././././. …, which looks weirld, put has .edu, looking safe to younger scratchers.How is ./ a problem?
Not yet a Knight of the Mu Calculus.
- helloandgoodbye9
-
 Scratcher
Scratcher
1000+ posts
Test for vulnerabilities please!
It hides that the url redirects to crashchrome. The browser ignores /./You may want to automatically remove /./ - https://blog.library.si.edu/./././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././redir.php?URL=http://crashcrome.com/ looks like blog.library.si.edu/././././././././././././././././././././././././. …, which looks weirld, put has .edu, looking safe to younger scratchers.How is ./ a problem?
Last edited by kaj (Tomorrow 25:61:61) ͪͪͪͪͪͪͪͪͪͪ ͣͣͣͣ ͯͯͯͯYes, its above the line)
- Jonathan50
-
 Scratcher
Scratcher
1000+ posts
Test for vulnerabilities please!
How does it “hide” it? I can still see the whole URL…It hides that the url redirects to crashchrome. The browser ignores /./You may want to automatically remove /./ - https://blog.library.si.edu/./././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././redir.php?URL=http://crashcrome.com/ looks like blog.library.si.edu/././././././././././././././././././././././././. …, which looks weirld, put has .edu, looking safe to younger scratchers.How is ./ a problem?
Not yet a Knight of the Mu Calculus.
- helloandgoodbye9
-
 Scratcher
Scratcher
1000+ posts
Test for vulnerabilities please!
Copy it into the block, then run it.How does it “hide” it? I can still see the whole URL…It hides that the url redirects to crashchrome. The browser ignores /./You may want to automatically remove /./ - https://blog.library.si.edu/./././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././redir.php?URL=http://crashcrome.com/ looks like blog.library.si.edu/././././././././././././././././././././././././. …, which looks weirld, put has .edu, looking safe to younger scratchers.How is ./ a problem?
Last edited by kaj (Tomorrow 25:61:61) ͪͪͪͪͪͪͪͪͪͪ ͣͣͣͣ ͯͯͯͯYes, its above the line)
- savaka
-
 Scratcher
Scratcher
1000+ posts
Test for vulnerabilities please!
The link shouldn't actually be blue because you can't click it, and the buttons should be a darker color when you hover on them, if you want it to be like ScratchX dialogs.
- NickyNouse
-
 Scratcher
Scratcher
1000+ posts
Test for vulnerabilities please!
Instead of truncating long urls, try putting the ellipses in the middle and showing the beginning and end of the URL.
- PullJosh
-
 Scratcher
Scratcher
1000+ posts
Test for vulnerabilities please!
Instead of truncating long urls, try putting the ellipses in the middle and showing the beginning and end of the URL.Interesting…
- CodingGamerHD
-
 Scratcher
Scratcher
62 posts
Test for vulnerabilities please!
*cough*
Maybe prevent using it in a forever loop?
when green flag clicked*cough*
forever
open page at url [http://www.randommalicioussite.com/] :: extension stack
end
Maybe prevent using it in a forever loop?
> Console.Write(get_os_ver(););
Running Ubuntu 16.10 (64-bit)/Windows 7 Ultimate SP1 (64-bit) (lives on as a VirtualBox VM)/Android 6.0, Google Chrome (no flash)
> Process.Start("https://scratch.mit.edu/users/CodingGamerHD/"); // Check out my projects!
> while (true) { Sharpy.Eat(new Kumquat.Evil(); }// This is my new pet Sharpy, Sharpy protects my siggy from siggy eating kumquats (alongside javascripty) by eating them! Payback, amirite?
>_
;
- NickyNouse
-
 Scratcher
Scratcher
1000+ posts
Test for vulnerabilities please!
*cough*Or maybe the option to "prevent this project from opening more websites [on this domain?]"when green flag clicked*cough*
forever
open page at url [http://www.randommalicioussite.com/] :: extension stack
end
Maybe prevent using it in a forever loop?
Last edited by NickyNouse (July 6, 2016 15:20:06)
- jackson4896
-
 New to Scratch
New to Scratch
1 post
Test for vulnerabilities please!
I tried adding And it just didn't work
- Ascold
-
 Scratcher
Scratcher
23 posts
Test for vulnerabilities please!
when green flag clicked
forever
open page at url [http:/scratch.mit.edu]
end
- Ascold
-
 Scratcher
Scratcher
23 posts
Test for vulnerabilities please!
When You Have No Gods, You Are Very Glad :
Last edited by Ascold (June 28, 2019 06:50:05)
- Cookiemousee
-
 Scratcher
Scratcher
99 posts
Test for vulnerabilities please!
I wish you could make it go to a link like this
go to webpage ( )
- _HAMSTER6_
-
 Scratcher
Scratcher
59 posts
Test for vulnerabilities please!
It Could Possibly Let People Link Other People To Disguised IP Grabbers
A bit of advice as you finished reading my post. Don't do SAND. SAND has four words.
SAND means Spam, Advertising, Necroposting, and Derailing.
Spam means posting something unrelated. Wiki Article: Spam
Advertising is when you promote your studios and projects. Wiki Article: Advertising
Necroposting is when you post on a old topic. It distracts other helpers! Wiki Article: Necroposting
Derailing is when you post something that leads others away from the topic. It is called thread hijacking. Wiki Article: Derailing
(Derailing idea comes from @Dude) (SAND is made by Nezon)
highlight all text and press ctrl + shift + down arrow keys

- Discussion Forums
- » Developing Scratch Extensions
-
» Test for vulnerabilities please!
![[RSS Feed] [RSS Feed]](//cdn.scratch.mit.edu/scratchr2/static/__74e70580e9dbe93ce1c3f8422dde592d__//djangobb_forum/img/feed-icon-small.png)